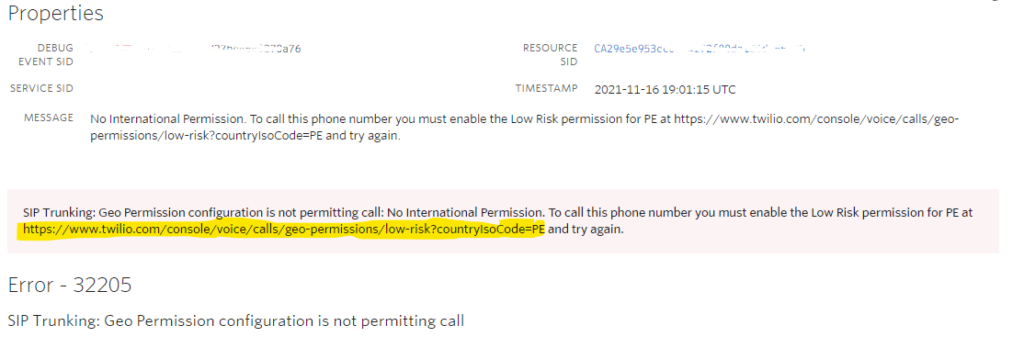
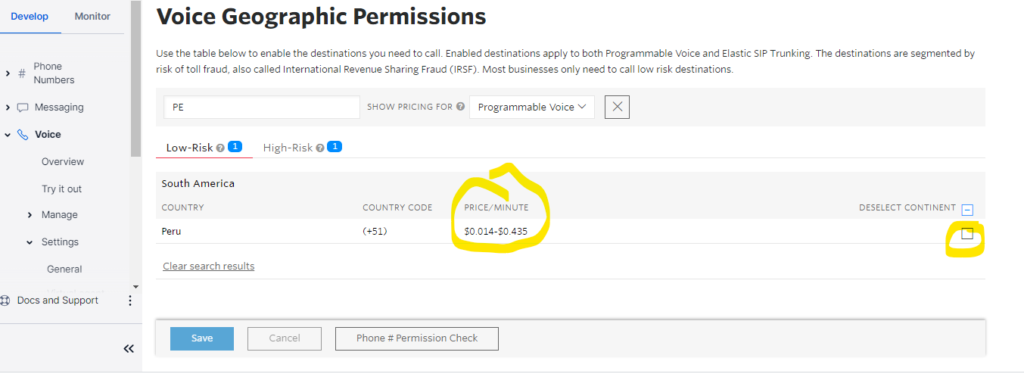
How to resolve issue with 3CX Tunnel ON 3CX PBX and 3CX Softphone (TNL)

Check the following things :
- Check your Softphone Settings (Steps Below).
- Check if you are able to ping the PBX server from LAN and outside LAN (Google How to ping a server from CMD/Terminal).
- Check your PBX settings (steps Below).
- Check your Internet connectivity.
- Check if any VPN/Firewall is blocking the services.

How to check 3cx Softphone Settings :
- Match if the 3cx Secure tunnel password and the username and password all match in your softphone to PBX.
- How to check if the username and password match in 3cx Softphone App :
- Go to your softphone and open the Account Settings
- Now click on the account you want to check and click on edit
- In case there is no profile please create a new profile on the softphone app.
- Now See if the Use 3cx Tunnel Option is Checked and match the passwords from here to your PBX.
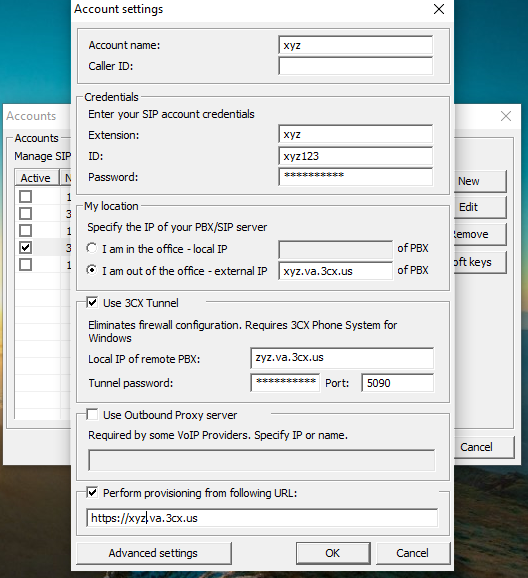
- How to check if the username and password match in 3cx Softphone App :

How to check 3cx PBX Settings :
- Match if the 3cx Secure tunnel password and the username and password all match in your PBX to Softphone.
- How to check if the username and password match in 3cx PBX .
- Go to your 3cx PBX admin login page and open the main menu from the left had side of the screen with 3 vertical bars if not already opened.
- Now click on the Security Dropdown menu :
- Here you will See the 3CX Tunnel Option. Click on it to open the settings.
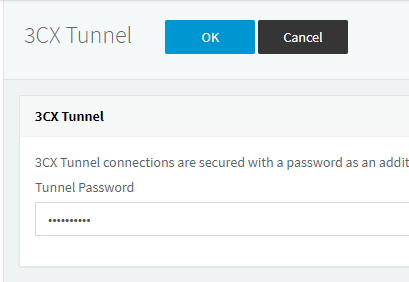
- This is your 3cx Tunnel Password which is different from your App username password.
- Copy this and match it from your softphone.
- Now Go to your PBX Main menu again from the left hand side and go to the users menu for configuring 3cx softphone settings.
- Now from the users menu open the extension you want to edit
- Now when the extension is opened go to phone provisioning tab
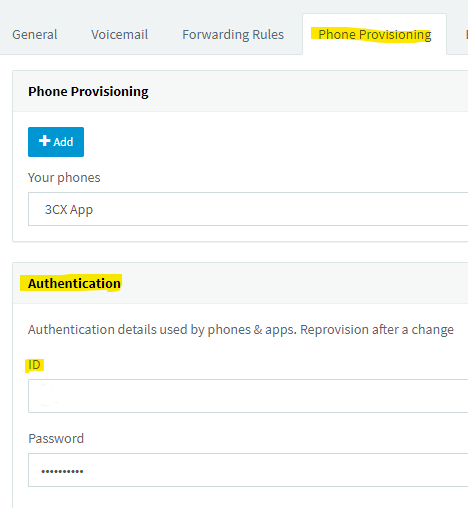
- Under the Authentication TAB is where you will Find your 3cx APP username and password.
- Match This from your softphone
- Now Go to the Options TAB
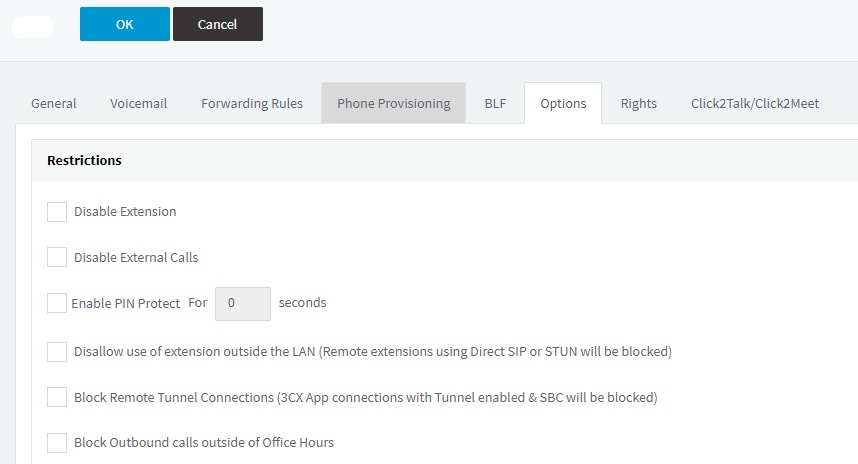
- Now in this Tab Check if the option Block Remote Tunnel Connections has been unchecked
- Also if the the extension is not disabled
- And if you are using the softphone outside the PBX local network then please check if the Disallow use of extension outside the LAN option is also unchecked
- How to check if the username and password match in 3cx PBX .

Downloads and links :
Download 3cx PBX from : https://www.3cx.com/pbx/
Download 3cx Softphone from : :https://www.3cx.com/voip/softphone/
You can Also find other config for Desk phones here : https://www.3cx.com/blog/voip-howto/configuring-sip-phone-as-tunnelled-external-extension/
We are using a cloud hosted Environment with and 3cx softphone app in the above case study.
Contact us or your network admin in case you require any more help.